📖 Word ("Phrase") of the Week: Mobile Device Management: Essential Security for Today's Law Practice 📱🔒
/Mobile Device Management is an essential concept for lawyers.
Mobile Device Management (MDM) has become essential for law firms navigating today's mobile-first legal landscape. As attorneys increasingly access confidential client information from smartphones, tablets, and laptops outside traditional office settings, MDM technology provides the security framework necessary to protect sensitive data while enabling productive remote work.
Understanding MDM in Legal Practice
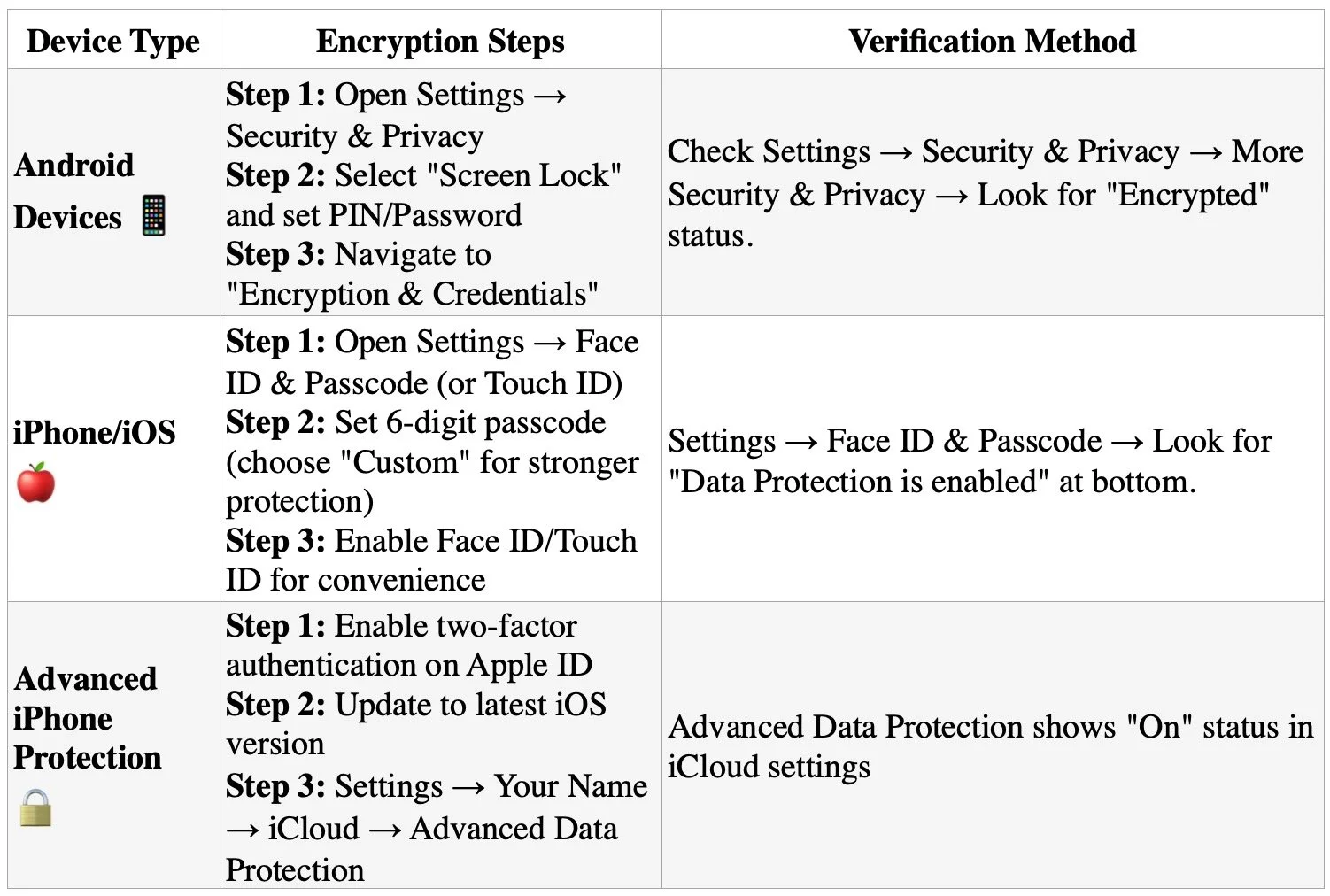
MDM refers to software that allows IT teams to remotely manage, secure, and support mobile devices used across an organization. For law firms, this technology provides centralized control to enforce password requirements, encrypt data, install security updates, locate devices, and remotely lock or wipe lost or stolen devices. These capabilities directly address the ethical obligations attorneys face under the ABA Model Rules of Professional Conduct.
Ethical Obligations Drive MDM Adoption
The legal profession faces unique ethical requirements regarding technology use. ABA Model Rule 1.1 requires lawyers to maintain technological competence, including understanding "the benefits and risks associated with relevant technology". Rule 1.6 mandates that lawyers "make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client".
ABA Formal Opinion 498 specifically addresses virtual practice considerations. The opinion cautions that lawyers should disable listening capabilities of smart speakers and virtual assistants while discussing client matters unless the technology assists the law practice. This guidance underscores the importance of thoughtful technology implementation in legal practice.
Core MDM Features for Law Firms
Device encryption forms the foundation of MDM security. All client data should be encrypted both in transit and at rest, with granular permissions determining who accesses specific information. Remote wipe capabilities allow immediate data deletion when devices are lost or stolen, preventing unauthorized access to sensitive case information.
Application management enables IT teams to control which applications can access firm resources. Maintaining an approved application list and regularly scanning for vulnerable or unauthorized applications reduces security risks. Containerization separates personal and professional data, ensuring client information remains isolated and secure even if the device is compromised.
Compliance and Monitoring Benefits
lawyers, do you know where your mobile devices are?
MDM solutions help law firms maintain compliance with ABA guidelines, state bar requirements, and privacy laws. The systems generate detailed logs and reports on device activity, which prove vital during audits or internal investigations. Continuous compliance monitoring ensures devices meet security standards while automated checks flag devices falling below required security levels.
Implementation Best Practices
Successful MDM implementation requires establishing clear policies outlining device eligibility, security requirements, and user responsibilities. Firms should enforce device enrollment and compliance, requiring all users to register devices before accessing sensitive systems. Multi-factor authentication enhances security for sensitive data access.
Regular training ensures staff understand security expectations and compliance requirements. Automated software updates and security patches keep devices protected against evolving threats. Role-based access controls prevent unauthorized access to corporate resources by assigning permissions based on job functions.
MDM technology has evolved from optional convenience to ethical necessity. Law firms that implement comprehensive MDM strategies protect client confidentiality, meet professional obligations, and maintain competitive advantage in an increasingly mobile legal marketplace.
Keep Your Practice Safe - Stay Tech Savvy!!!