TSA permits power banks up to 100Wh (approximately 27,000mAh) in carry-on luggage. Anker Prime Power Bank* (26K, 300W) offers exceptional capacity at 26,250mAh, providing powerful performance for simultaneous device charging while meeting TSA requirements. The smart display provides real-time insights into charging speed and battery levels, with dual USB-C ports delivering 140W maximum output per port. This enables charging a MacBook Pro while simultaneously powering an iPhone and iPad—essential during multi-hour delays where multiple devices require constant connectivity.
For lighter travel, the Anker 747 Power Bank (PowerCore 26K) delivers 25,600mAh capacity with 87W rapid charging in a more compact profile. Budget-conscious travelers find the Anker MagGo* series offers excellent value as the best travel-specific Anker option. All Anker models feature multiple charging ports, allowing lawyers to charge phones, tablets, and laptops simultaneously—critical when airport charging stations become competition zones during this crisis.
Note: If you are going to plug into an available outlet, don’t forget to use a serge protector. A sudden change in current could wipe out your device and leave you in a pickle.
Document Scanning: Adobe Technology on Your Apple Devices
Adobe Document Cloud transforms smartphones and tablets into powerful document management systems. The Adobe Scan app on iPhone and iPad uses optical character recognition to convert printed documents into searchable, editable PDFs. The app automatically detects document edges, straightens images, and enhances text clarity—perfect for scanning contracts, pleadings, or client intake forms from any location.
Adobe Acrobat Reader on iPhone, iPad, and Mac provides seamless document access across your entire Apple ecosystem. Documents opened on your MacBook sync instantly to your iPad or iPhone, allowing you to continue working on depositions notes from your phone during airport delays. The integrated fill-and-sign functionality enables you to execute agreements while in transit, with e-signatures recognized across all Adobe Document Cloud platforms. Importantly, Adobe products maintain cloud synchronization—if you lose cellular connection, previously downloaded documents remain accessible, ensuring you can work offline during flights or in coverage dead zones.youtube
Practice Management: Download Before You Depart
Cloud-based platforms like Clio enable remote access to case files, time tracking, and client communications from any device. The critical step traveling lawyers often overlook: download all necessary files to your device BEFORE leaving the office. Modern practice management apps allow offline access to downloaded content, ensuring you maintain full productivity even if cellular or Wi-Fi connectivity fails. Flight time, extended airport delays, and coverage-restricted locations won't interrupt your work if essential files are already stored locally. Enable offline mode in your practice management app before traveling, treating it as a mandatory pre-departure checklist item alongside your boarding pass.
Noise-Cancelling Headphones for Focus
Sony WH-1000XM5 and Bose QuietComfort Ultra headphones provide 30-40 hour battery life and industry-leading active noise cancellation. I personally am a fan of Apple AirPods Max* (for flights) and Apple AirPods* (for on the go). These tools enable concentration during flights and allow productive conference calls from crowded gate areas. Budget options like Soundcore Life Q30 deliver comparable performance at reduced cost.
The Apple Ecosystem Advantage for Traveling Lawyers
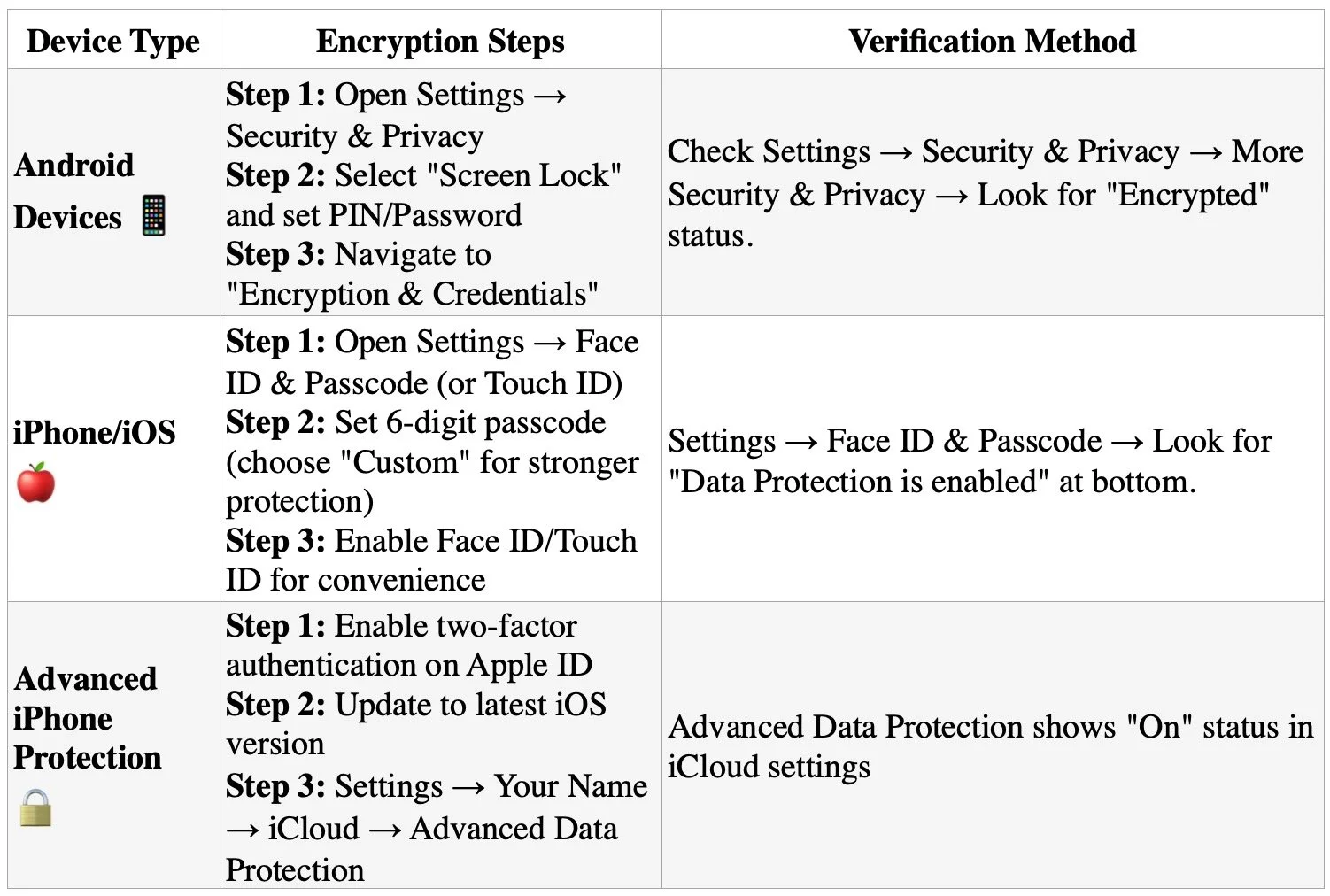
Seamless integration across iPhone, iPad, and MacBook enables efficiency that standalone devices cannot match. Lawyers leveraging the Apple ecosystem can start a document review on their MacBook, switch to an iPad for annotation during client meetings, and finalize on an iPhone while traveling between appointments. This continuity proves invaluable during travel disruptions when flexibility matters most. Security features including Touch ID, Face ID, and FileVault encryption protect client confidentiality. The closed ecosystem provides transparency and security that appeals to legal professionals handling sensitive information.
TSA PreCheck and Global Entry
While not technology per se, these trusted traveler programs dramatically reduce security wait times—increasingly critical as TSA operates with reduced staffing. PreCheck costs $78 for five years; Global Entry includes PreCheck benefits plus expedited customs for $100 per five years. Applications require background checks and in-person interviews, so apply well before travel needs arise.
Prepare Before You Depart