🎙️ Ep. 122: Cybersecurity Essentials for Law Firms: Proven Strategies from Navy Veteran & Attorney Cordell Robinson
/My next guest is Cordell Brion Robinson, CEO of Brownstone Consulting Firm and a decorated US Navy veteran who brings an extraordinary combination of expertise to cybersecurity. With a background in Computer Science, Electrical Engineering, and law, plus experience as a Senior Intelligence Analyst, Cordell has created cybersecurity programs that comply with the National Institute of Standards and Technology, the Federal Information Security Management Act, and the Office of Management and Budget standards for both government and commercial organizations. His firm specializes in compliance services, performing security framework assessments globally for commercial and government entities. Currently, he's innovating the cybersecurity space through automation for security assessments. Beyond his professional accomplishments, Cordell runs the Shaping Futures Foundation, a nonprofit dedicated to empowering youth through education, demonstrating his commitment to giving back to the community.
Join Cordell Robinson and me as we discuss the following three questions and more! 🎙️
1. What are the top three cybersecurity practices that lawyers should immediately adopt to secure both client data and sensitive case material in their practice?
2. From your perspective as both a legal and cybersecurity expert, what are the top three technology tools or platforms that can help lawyers streamline compliance and governance requirements in a rapidly evolving regulatory environment?
3. What are the top three steps lawyers can take to overcome resistance to technology adoption in law firms, ensuring these tools actually improve outcomes and efficiency rather than just adding complexity
In our conversation, we cover the following: ⏱️
- 00:00:00 - Introduction and welcome to the podcast
- 00:00:30 - Cordell's current tech setup - Windows laptop, MacBook, and iPhone
- 00:01:00 - iPhone 17 Pro Max features including 48MP camera, 2TB storage, and advanced video capture
- 00:01:30 - iPhone 17 Air comparison and laptop webcam discussion
- 00:02:00 - VPN usage strategies - Government VPN for secure client communications
- 00:02:30 - Commercial client communications and secure file sharing practices
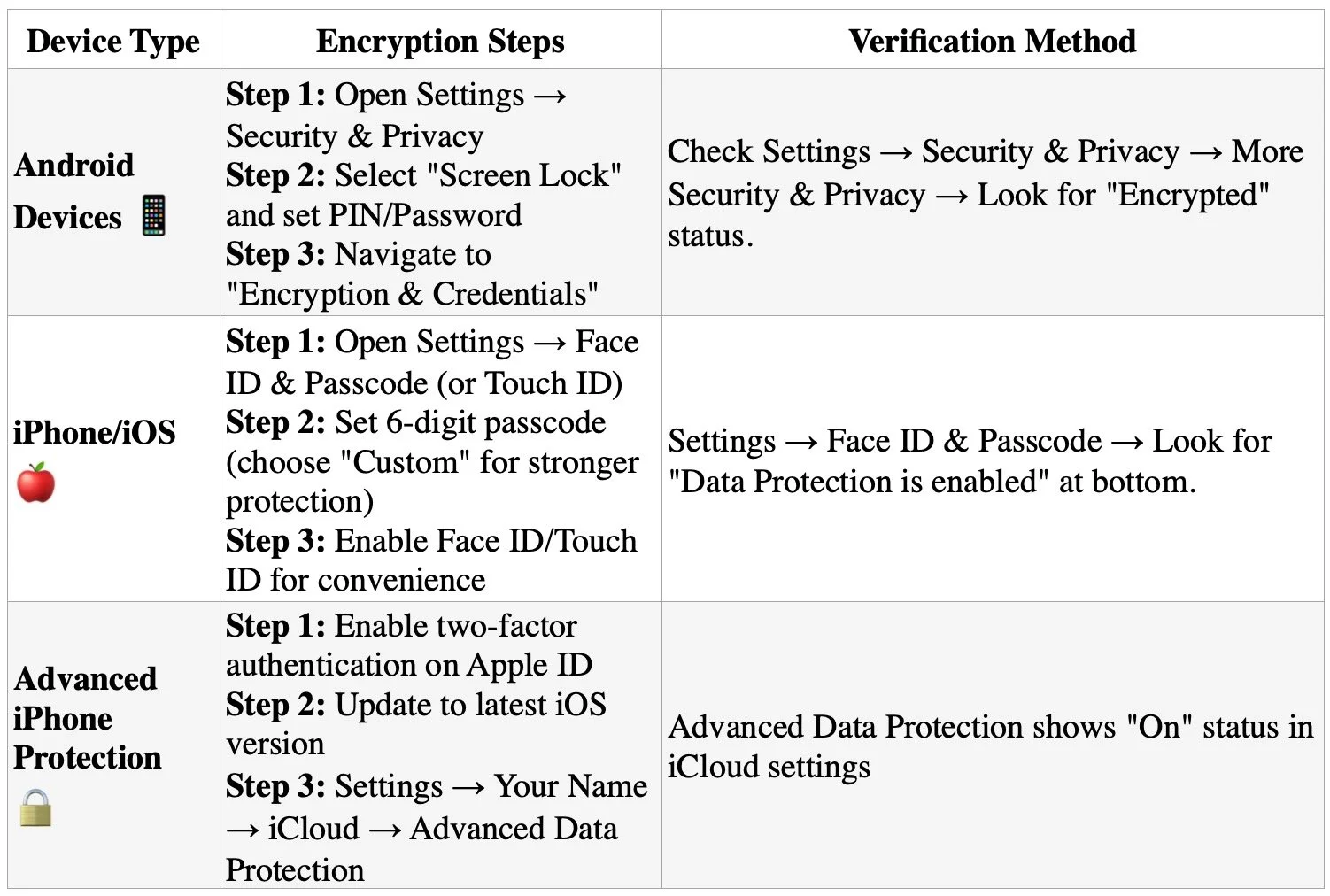
- 00:03:00 - Why email encryption matters and Mac Mail setup tutorial
- 00:04:00 - Bonus question: Key differences between commercial and government security work
- 00:05:00 - Security protocols comparison and navigating government red tape
- 00:06:00 - Question 1: Top three cybersecurity practices lawyers must implement immediately
- 00:06:30 - Understanding where client data comes from and having proper IT security professionals
- 00:07:00 - Implementing cybersecurity awareness training for all staff members
- 00:07:30 - Practical advice for solo and small practitioners without dedicated IT staff
- 00:08:00 - Proper email practices and essential security awareness training skills
- 00:08:30 - Handling data from average clients in sensitive cases like family law
- 00:09:00 - Social engineering considerations in contentious legal matters such as divorces
- 00:10:00 - Screening threats from seemingly reliable platforms - Google Play slop ads as recent example
- 00:10:30 - Tenable vulnerability scanning tool recommendation (approximately $1,500/year)
- 00:11:00 - Question 2: Technology tools for streamlining compliance and governance
- 00:11:30 - GRC tools for organizing compliance documentation across various price points
- 00:12:00 - SharePoint security lockdown and importance of proper system configuration
- 00:12:30 - Monitoring tools discussion - why no perfect solution exists and what to consider
- 00:13:00 - Being amenable to change and avoiding long-term contracts with security tools
- 00:14:00 - Question 3: Strategies for overcoming resistance to technology adoption
- 00:14:30 - Demonstrating efficiency and explaining the full implementation process
- 00:15:00 - Converting time savings to dollars and cents for senior attorney buy-in
- 00:15:30 - Mindset shift for billable hour attorneys and staying competitive in the market
- 00:16:00 - Being a technology Guinea pig and testing tools yourself first
- 00:16:30 - Showing real results to encourage buy-in from colleagues
- 00:17:00 - Real-world Microsoft Word example - styles, cross-references, and table of contents time savings
- 00:17:30 - Showing value add and how technology can bring in more revenue
- 00:18:00 - Where to find Cordell Robinson - LinkedIn, www.bcf-us.com, Brownstone Consulting Firm
- 00:18:30 - Company description and closing remarks
Resources 📚
Connect with Cordell Robinson:
Company Website: https://www.bcf-us.com
Instagram: https://www.instagram.com/brownstone_consulting_firm
Shaping Futures Foundation: https://shapingfutures.org
Government & Compliance Frameworks:
NIST: https://www.nist.gov
NIST Time Services: https://nist.time.gov
Software & Tools:
Apple Mail Encryption Guide: https://support.apple.com/guide/mail/sign-or-encrypt-emails-mlhlp1180/mac
Apple Products: https://www.apple.com
Microsoft SharePoint: https://www.microsoft.com/en-us/microsoft-365/sharepoint/collaboration
Microsoft Word: https://www.microsoft.com/en-us/microsoft-365/word
Tenable Vulnerability Management: https://www.tenable.com