🚨 BOLO: Solo and Small Law Firms Lag in AI Adoption: Key Insights from ClioCon 2025 and Steps Forward
/Solo and Small Law Firms Falling Behind in AI Adoption: Insights from ClioCon 2025 and How to Close the Gap
Read MoreSolo and Small Law Firms Falling Behind in AI Adoption: Insights from ClioCon 2025 and How to Close the Gap
Read More
224 Malicious Android Apps Detected – Lawyers Must Act Now to Protect Client Data!
Recent cybersecurity intelligence reveals that 224 malicious Android applications successfully circumvented Google Play Store's anti-malware systems through a sophisticated campaign dubbed "SlopAds". This represents a significant escalation in mobile security threats that demands immediate attention from legal professionals who increasingly rely on mobile devices for client communications and case management.
The Threat Mechanism 🎯
The SlopAds campaign employs a cunning two-stage attack strategy. When users download these applications directly from Google Play Store searches, they function as advertised. However, apps downloaded via targeted advertising campaigns secretly install encrypted configuration files that subsequently deploy malware onto devices. This technique successfully evaded Google's standard security reviews by appearing benign during initial screening.
The malicious applications typically masqueraded as simple utilities or attempted to impersonate popular applications like ChatGPT. Once activated, the malware harvests device information and generates fraudulent advertising impressions, potentially compromising sensitive data and device integrity.
Why Legal Professionals Face Elevated Risk ⚖️
Legal practitioners encounter disproportionate cybersecurity risks due to several converging factors. Law firms handle exceptionally sensitive data including privileged attorney-client communications, merger and acquisition details, intellectual property, medical records, and confidential case strategies. This makes legal professionals prime targets for sophisticated threat actors seeking valuable information.
Recent data indicates that over 110 law firms reported data breaches in 2022 alone, exceeding previous years and demonstrating an escalating trend. The consequences of mobile device compromise extend beyond data theft to include potential malpractice liability, ABA ethics violations under Model Rules 1.1 (Competence), 1.1(8) (Tech Competence) and 1.6 (Confidentiality), state bar disciplinary action, regulatory compliance fines, and permanent reputational damage.
Mobile devices present particularly acute risks because they often contain both personal and professional data, blur the boundaries between work and personal use, and are easily misplaced or stolen. Interestingly, twenty-five percent of data breaches in financial services since 2006 resulted from lost or stolen devices, highlighting the vulnerability of mobile platforms.
Comprehensive Protection Strategy 🛡️
Immediate Device Security Measures

Law Firm Cybersecurity Framework: Policies, Training, and Incident Response for Mobile Threats.
Enable full-device encryption on all smartphones and tablets used for any professional purposes. This critical step ensures that even if devices are physically compromised, sensitive data remains protected. Modern Android devices (version 6.0+) and iPhones automatically enable encryption when a screen lock is configured, but verification and proper setup remain essential.
Critical Implementation Notes
Android devices must remain plugged into power during the encryption process, which takes approximately one hour and cannot be interrupted;
Choose complex passcodes rather than simple PINs or patterns - six-digit minimum for iPhones, with alphanumeric options preferred;
Most devices since Android 6.0 and iOS 8 enable encryption by default when screen locks are configured, but manual verification is essential;
For maximum security on iPhones, enable the "Erase Data" feature after 10 failed attempts for devices containing highly sensitive information.
Implement strong, unique passwords or biometric authentication rather than simple PINs or patterns. The encryption key derives directly from your lock screen credentials, making password strength critical for data protection. For legal professionals handling privileged communications, this represents the first line of defense against unauthorized access to confidential client information.
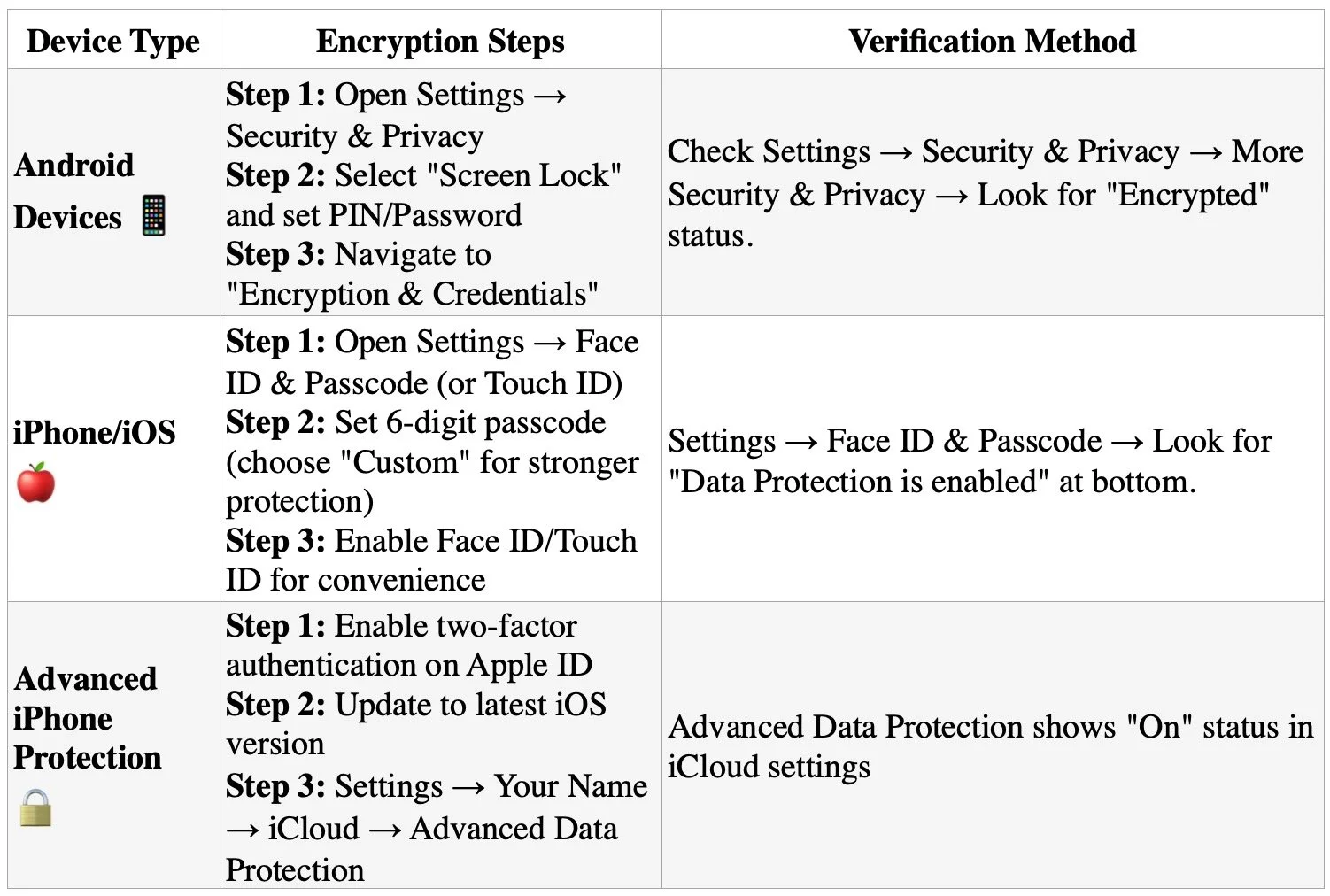
some stepts to Enable full-device encryption on all smartphones and tablets used for any professional purposes.
Application Security Protocols
Download applications exclusively from official app stores and carefully review all requested permissions before installation. Be particularly vigilant about apps requesting "Display over other apps" permissions, as these can enable malware to hijack device functionality. Remove any unused applications regularly and avoid third-party app stores entirely.
Mobile Device Management (MDM) Implementation
Deploy comprehensive MDM solutions that enforce security policies across all firm devices. MDM systems should include capabilities for remote data wiping, automatic security updates, app blacklisting, and real-time threat detection. These systems provide centralized control over device security while maintaining user productivity.
Authentication and Access Controls
Mandate multi-factor authentication (MFA) for all professional applications and accounts. Use authentication apps or hardware tokens rather than SMS-based codes, which can be intercepted. Implement biometric authentication where available for an additional security layer.
Network Security Measures
Utilize Virtual Private Networks (VPNs) when accessing firm resources from public Wi-Fi networks. Ensure all communications involving client data occur through encrypted channels such as secure client portals rather than standard email or messaging applications.
Advanced Protection Considerations 🔍
Regular Security Assessments

BE Your firm’s heao! Know the Essential Mobile Security Protocols Every Lawyer Needs: Encryption, MFA, and VPN Protection!
Perform periodic security audits of all mobile devices and applications used within the firm. These assessments should identify vulnerabilities, ensure compliance with security policies, and evaluate the effectiveness of existing protections.
Secure Communication Channels
Implement client portals and secure messaging platforms specifically designed for legal communications. These systems provide encrypted data transmission and storage while maintaining audit trails for compliance purposes.
Data Backup and Recovery
Maintain regular, encrypted backups of all mobile device data with tested recovery procedures. This ensures business continuity in case of device compromise or loss while protecting sensitive information.
The SlopAds malware campaign demonstrates that traditional security assumptions about official app stores no longer provide adequate protection. Legal professionals must adopt a comprehensive, multi-layered approach to mobile security that addresses both technical vulnerabilities and human factors. By implementing these protective measures proactively, law firms can significantly reduce their exposure to mobile-based cyber threats while maintaining the productivity benefits of mobile technology.
Stay Safe Out There!

you'RE not alone if you are having pacer log-in issues!
Lawyers frustrated with PACER login problems are not alone. The PACER Service Center (PSC) recently announced ongoing challenges as it rolls out new security standards, including stronger password requirements and multifactor authentication (MFA). These efforts are designed to better protect account security, but they have also created long call wait times and confusion for attorneys nationwide.
According to a September 2025 notice, the PSC has temporarily delayed enforcing the updated password requirements in order to reduce congestion and ease the transition. Importantly, not all users are required to take immediate action. Only those who are directly prompted to enroll in MFA upon logging in should do so. If you are not prompted, no changes are necessary yet, and courts strongly encourage attorneys to avoid calling the PSC unless required. Instead, lawyers should review the MFA Tips and Resources list before contacting support.

Lawyers need to keep up to date if they are having issues logging into the federal court filing system!
Attorneys are also invited to provide feedback on the MFA process and options through a short online survey. This feedback will help the PSC refine authentication practices while balancing security and accessibility needs. Because PACER access is central to case management, e-filing, and real-time tracking of federal litigation, attorneys should pay close attention to these developments.
As the practice of law continues to adopt digital tools, maintaining secure, reliable access to PACER is critical. Staying informed by following your favorite The Tech-Savvy Lawyer or PACER Resources, and by following official guidance and taking proactive steps, attorneys can ensure they remain efficient and compliant in today’s evolving legal tech environment. ⚖️📲
🔐 The Uncomfortable Truth About Court Filing Security 📊

Federal court filing systems are under attack! Are your client’s information protected?!
The federal judiciary's electronic case management system (CM/ECF) and PACER have been described as "unsustainable due to cyber risks". This isn't hyperbole – it's the official assessment from federal court officials who acknowledge that these systems, which legal professionals use daily for document uploads and case management, face "unrelenting security threats of extraordinary gravity".
Recent breaches have exposed sealed court documents, including confidential informant identities, arrest warrants, and national security information. Russian state-linked actors are suspected in these intrusions, which exploited security flaws that have been known since 2020. The attacks were described by one federal judiciary insider as being like "taking candy from a baby".
Human Error: The Persistent Vulnerability 🎯
Programs like #ILTACON2025’s "Anatomy of a Cyberattack" demonstrations that draw packed conference rooms highlight a critical truth: 50% of law firms now identify phishing as their top security threat, surpassing ransomware for the first time. This shift signals that cybercriminals have evolved from automated malware to sophisticated human-operated attacks that exploit our psychological weaknesses rather than just technical ones.
Consider these sobering statistics: 29% of law firms experienced security breaches in 2023, with 49% of data breaches involving stolen credentials. Most concerning is that only 58% of law firms provide regular cybersecurity training to employees, leaving the majority vulnerable to the very human errors that sophisticated attackers are designed to exploit.
What Lawyers Must Do Immediately 🛡️

Model rules require lawyers be aware of electronic court filing “insecurities”!
First, acknowledge that your court filings are not secure by default. The federal court system has implemented emergency procedures that require highly sensitive documents to be filed on paper or on secure devices, rather than through electronic systems. This should serve as a wake-up call about the vulnerabilities inherent in digital filing processes.
Second, implement multi-factor authentication everywhere. Despite its critical importance, 77% of law firms still don't use two-factor authentication. The federal courts only began requiring this basic security measure in May 2025 – decades after the technology became standard elsewhere.
Third, encrypt everything. Only half of law firms use file encryption, and just 40% employ email encryption. Given that legal professionals handle some of society's most sensitive information, these numbers represent a profound failure of professional responsibility.
Beyond Basic Defenses 🔍
Credential stuffing attacks exploit password reuse across platforms. When professionals use the same password for their court filing accounts and personal services, a breach anywhere becomes a breach everywhere. Implement unique, complex passwords for all systems, supported by password managers.
Cloud misconfiguration presents another critical vulnerability. Many law firms assume their technology providers have enabled security features by default, but the reality is that two-factor authentication and other protections often require explicit activation. Don't assume – verify and enable every available security feature.
Third-party vendor risks cannot be ignored. Only 35% of law firms have formal policies for managing vendor cybersecurity risks, yet these partnerships often provide attackers with indirect access to sensitive systems.
The Compliance Imperative 📋
The regulatory landscape is tightening rapidly. SEC rules now require public companies to disclose material cybersecurity incidents within four business days. While this doesn't directly apply to all law firms, it signals the direction of regulatory expectations. Client trust and professional liability exposure make cybersecurity failures increasingly expensive propositions.
Recent class-action lawsuits against law firms for inadequate data protection demonstrate that clients are no longer accepting security failures as inevitable business risks. The average cost of a legal industry data breach reached $7.13 million in 2020, making prevention significantly more cost-effective than remediation.
Final Thoughts: A Call to Professional Action ⚖️

Lawyers are a first-line defender of their client’s protected information.
The cybersecurity sessions are standing room only because lawyers are finally recognizing what cybersecurity professionals have known for years: the threat landscape has fundamentally changed. Nation-state actors, organized crime groups, and sophisticated cybercriminals view law firms as high-value targets containing treasure troves of confidential information.
The federal court system's acknowledgment that its filing systems require complete overhaul should prompt every legal professional to audit their own digital security practices. If the federal judiciary, with its vast resources and expertise, struggles with these challenges, individual practitioners and firms face even greater risks.
The legal profession's ethical obligations to protect client confidentiality extend into the digital realm. See ABA Model Rules 1.1, 1.1(8), and 1.6. This isn't about becoming cybersecurity experts – it's about implementing reasonable safeguards commensurate with the risks we face. When human error remains the biggest vulnerability, the solution lies in better training, stronger systems, and a cultural shift that treats cybersecurity as a core professional competency rather than an optional technical consideration.
The standing-room-only cybersecurity sessions reflect a profession in transition. The question isn't whether lawyers need to take cybersecurity seriously – recent breaches have answered that definitively. The question is whether we'll act before the next breach makes the decision for us. 🚨

Android users must be aware of potential threats to their data!
CRITICAL THREAT ALERT 🚨 A sophisticated new Android spyware campaign dubbed LunaSpy has been active since February 2025, broadly targeting Android users via messaging apps—anyone installing its fake “antivirus” could be compromised, including legal professionals. LunaSpy spreads through Telegram, WhatsApp, Signal, and other platforms by sending messages like “Hi, install this program here,” tricking victims into granting extensive device permissions after fake security scans report fabricated threats.
Once installed, LunaSpy’s capabilities pose severe risks: it steals passwords from browsers and messaging apps, intercepts text messages (including two-factor codes), records audio and video via microphones and cameras, captures screen contents (e.g., client documents, case notes), and tracks real-time location (e.g., revealing meetings and court visits). Kaspersky researchers have linked over 150 command-and-control servers to LunaSpy’s global network, enabling continuous data exfiltration and remote command execution.
While any Android user is at risk, lawyers face heightened consequences if infected. A breach of attorney-client communications or privileged documents can trigger:
Malpractice liability for failing to safeguard confidential client information
ABA ethics violations under Model Rules 1.1 (Competence), 1.1(8) (Maintaining Competence) and 1.6 (Confidentiality)
State bar disciplinary action for professional misconduct
Regulatory compliance fines under privacy laws like California Consumer Privacy Act (CCPA)/General Data Protection Regulation (GDPR) – Legal Text
Reputational damage that can permanently erode client trust
Immediate Action Steps for all Android-using legal professionals and their staff:

users are the first line of defense when it comes to preventing computer viruses on their tech!
Audit and remove any unverified security or banking apps; restrict installations to Google Play only.
Deploy Mobile Device Management (MDM): enforce app blacklists, remote wipe, and automated patching.
Enable full-disk encryption and secure lock screens with complex passcodes or biometrics.
Train staff on social engineering tactics—recognize unsolicited install prompts or links in messages.
Use end-to-end encrypted desktop-based messaging for privileged communications, limiting mobile use.
Establish an incident response plan: include immediate device quarantine, forensic analysis, and regulatory notification procedures.
LunaSpy is not a hypothetical risk—it’s actively compromising Android devices around the globe. Although the campaign targets the general public, legal professionals handling sensitive client data are particularly vulnerable to cascading professional, legal, and ethical consequences if infected. With over 150 active command servers and ongoing code enhancements, the threat will only escalate. Every day without these safeguards increases your exposure—act now to secure mobile devices, train teams, and reinforce your firm’s cybersecurity posture.
Critical browser flaw affects Windows & Apple devices. Attackers escape Chrome's sandbox via malicious web pages. ACTIVELY EXPLOITED.

Lawyers its generally a good idea to keep your software up-to-date in order to prevent security risks!
🔍 WHAT THIS MEANS IN PLAIN TERMS:
Your browser normally acts like a protective barrier between dangerous websites and your computer's files. This vulnerability is like a secret door that bypasses that protection. When you visit a compromised website, even legitimate sites that have been hacked, criminals can potentially access your client files, emails, and sensitive data without you knowing. The attack happens silently in the background while you browse normally.
⚠️ ACTION REQUIRED:
🚨Legal Risks:
✓ Client confidentiality breaches
✓ ABA ethical violations
✓ Malpractice liability
✓ Trust account exposure
Don't wait - update NOW!

lawyers were your client’s pii hacked from your computers and software?
Lawyers across the nation need to take immediate action following the exposure of 16 billion login credentials—covering platforms from Apple and Google to Facebook and countless others—in what researchers describe as one of the largest exposures of sensitive data in history. While headlines have suggested a catastrophic, single-source breach, the reality is more nuanced but equally concerning for legal professionals. This leak is not a new, isolated hack of a major provider. Instead, it's a massive aggregation of credentials collected over years from various infostealer malware campaigns and previous breaches, now compiled and exposed in over 30 datasets.
What Is the Nature of This Breach? Is It "New"? 🕵️♂️
The so-called "16 billion password breach" is not the result of a single event. Instead, it's a compilation of old and some recent credentials, gathered from infostealer malware, credential stuffing lists, and previously leaked databases. Some datasets are fresh and weaponizable, including session tokens and cookies that can bypass multi-factor authentication, but much of the data is recycled or duplicated. The scale, however, means nearly every major online service is potentially implicated, and the risk of credential stuffing and account takeover is real—especially for those who reuse passwords or have not updated them in years.
Why Should Lawyers Care? ⚠️
Lawyers are high-value targets for cybercriminals due to the sensitive nature of client data and privileged communications. The legal profession has already seen significant cybersecurity challenges, with 29% of law firms encountering cybersecurity breaches in 2023, and the average cost of a data breach for law firms reaching $5.08 million. A compromised password can lead to unauthorized access to confidential files, emails, and client records, exposing firms to malpractice claims, regulatory penalties, and reputational harm. The legal sector's increasing reliance on cloud platforms and digital workflows makes robust credential management non-negotiable for lawyers.
What Should Lawyers Do Now? 🛡️
Immediate Steps:
Reset passwords for any account that may be affected, especially if you reuse passwords across sites.
Check your exposure using tools like "Have I Been Pwned" to see if your email or credentials are part of known breaches.
Enable Multi-Factor Authentication (MFA) on all accounts—this is the single most effective way to prevent unauthorized access, even if a password is leaked.
Long-Term Best Practices:
Adopt a password manager (such as 1Password* or similar) to generate and store unique, complex passwords for every account.
Educate your staff on phishing, social engineering, and the dangers of password reuse.
Implement passkeys and biometrics where possible, reducing reliance on passwords alone.
Regularly monitor for compromised credentials using security tools and services that alert you to new breaches.
Never store passwords in plaintext or unsecured documents; use encrypted vaults and secure delivery for sensitive credentials.
What Should Law Firms and Lawyers Be Doing to Stay Secure? 🏛️

Lawyers need to be active in protecting their client’s pii!
Review and update firm-wide password policies to mandate unique, strong passwords and regular changes.
Ensure all devices and cloud services used for legal work are protected with MFA and monitored for suspicious activity.
Consult with cybersecurity counsel or specialists to assess your firm's exposure and compliance with data protection regulations.
Stay informed about new threats and regularly audit your digital security posture.
Essential Resources from The Tech-Savvy Lawyer 📚🎧
For deeper insights into cybersecurity best practices for legal professionals, explore these valuable resources from The Tech-Savvy Lawyer.Page:
Blog Posts:
"🚨 BOLO: Zoom Remote Access Attacks – Critical Security Alert for Legal Professionals 🚨" - Learn about sophisticated cyberattacks targeting legal professionals through video conferencing platforms and how to protect your practice.
"BOLO: Is LastPass on its Last Leg?! 🧐 Is it time to get a new password manager? 😳" - Essential guidance on password manager security following the LastPass breach, with recommendations for alternative solutions like 1Password.
"🚨 BOLO: Apple's Latest Update Activates AI - Lawyers, Protect Your Clients' Data! 🚨" - Critical analysis of how automatic AI features can impact attorney-client privilege and data security.
Podcast Episodes:
🎙️ Ep. 104: The Importance of Data Backup & Cybersecurity w "Mr. Backup", Curtis Preston! - Expert insights on what lawyers are doing wrong with cybersecurity, e-discovery best practices, and ransomware response strategies.
🎙️ Ep. 106: "How Lawyers Can Protect Client Data in the Age of AI - A conversation with Erich Dylus!" - Essential guidance on maintaining client confidentiality while leveraging AI tools.
🎙️Episode 99: "Navigating the Intersection of Law Ethics and Technology with Jayne Reardon" - Practical insights for lawyers with limited to moderate tech skills on strategic legal tech adoption.
These resources provide actionable guidance specifically tailored for legal professionals navigating cybersecurity challenges while maintaining ethical obligations under the ABA Model Rules.
Lawyers Must Act Now - Your Practice's Security Is Your Clients' Trust 🔐

Follow The Tech-Savvy Lawyer.Page for breaking news and bolos that lawyers need to know!
The 16 billion password leak serves as a stark reminder that cybersecurity is not optional for today's legal professionals—it's an ethical imperative that lawyers cannot ignore. While this massive data aggregation may seem overwhelming, it presents an opportunity for lawyers to strengthen their firm's digital defenses and demonstrate their commitment to protecting client confidentiality.
Remember, as outlined in ABA Model Rule 1.1, Comment 8, lawyers must maintain reasonable competency in technology, including understanding "the benefits and risks associated with relevant technology". The steps outlined above are not just technical recommendations for lawyers—they're essential components of competent legal representation in the digital age.
By implementing robust password policies, enabling multi-factor authentication, and staying informed through resources like The Tech-Savvy Lawyer.Page, lawyers are not just protecting data—they're preserving the foundational trust that defines the attorney-client relationship. In an era where cyber threats evolve daily and law firms face increasing risks, lawyers' proactive approach to cybersecurity becomes a competitive advantage and a mark of professional excellence.
Lawyers must take action today. Your clients' trust—and your practice's future—depend on it.

LAWYERS NEED TO BE BOTH TECH-SAVVY AND Cyber-SavvY!
On December 25, 2024, LexisNexis Risk Solutions (LNRS)—a major data broker and subsidiary of LexisNexis—suffered a significant data breach that exposed the personal information of over 364,000 individuals. This incident, which went undetected until April 2025, highlights urgent concerns for legal professionals who rely on LexisNexis and its related products for research, analytics, and client management.
What Happened in the LexisNexis Breach?
Attackers accessed sensitive data through a third-party software development platform (GitHub), not LexisNexis’s internal systems. The compromised information includes names, contact details, Social Security numbers, driver’s license numbers, and dates of birth. Although LexisNexis asserts that no financial or credit card data was involved and that its main systems remain secure, the breach raises red flags about the security of data handled across all Lexis-branded platforms.
Why Should You Worry About Other Lexis Products?
LexisNexis Risk Solutions is just one division under the LexisNexis and RELX umbrella, which offers a suite of legal, analytics, and data products widely used by law firms, courts, and corporate legal departments. The breach demonstrates that vulnerabilities may not be limited to one product or platform; third-party integrations, development tools, and shared infrastructure can all present risks. If you use LexisNexis for legal research, client intake, or case management, your clients’ confidential data could be at risk—even if the breach did not directly affect your specific product.
Ethical Implications: ABA Model Rules of Professional Conduct

ALL LawyerS NEED TO BE PREPARED TO FighT Data LeakS!
The American Bar Association’s Model Rules of Professional Conduct require lawyers to safeguard client information and maintain competence in technology. Rule 1.6(c) mandates that attorneys “make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client.” Rule 1.1 further obligates lawyers to keep abreast of changes in law and its practice, including the benefits and risks associated with relevant technology.
In light of the LexisNexis breach, lawyers must:
Assess the security of all third-party vendors, including legal research and data analytics providers.
Promptly notify clients if their data may have been compromised, as required by ethical and sometimes statutory obligations.
Implement additional safeguards, such as multi-factor authentication and regular vendor risk assessments.
Stay informed about ongoing investigations and legal actions stemming from the breach.
What Should Legal Professionals Do Next?
Review your firm’s use of LexisNexis and related products.
Ask vendors for updated security protocols and breach response plans.
Consider offering affected clients identity protection services.
Update internal policies to reflect heightened risks associated with third-party platforms.
The Bottom Line
The LexisNexis breach is a wake-up call for the legal profession. Even if your primary Lexis product was not directly affected, the interconnected nature of modern legal technology means your clients’ data could still be at risk. Proactive risk management and ethical vigilance are now more critical than ever.

Defend Client Data from Malware!
The discovery of the “Kaleidoscope” ad fraud malware targeting Android devices is a wake-up call for legal professionals. This threat, which bombards users with unskippable ads and exploits app permissions, is not just an annoyance - it is a direct risk to client confidentiality, law firm operations, and compliance with the ABA Model Rules of Professional Conduct. Lawyers must recognize that cybersecurity is not optional; it is an ethical mandate under the ABA Model Rules, including Rules 1.1, 1.3, 1.4, 1.6, 5.1, and 5.3.
Why the ABA Model Rules Matter
Rule 1.6 (Confidentiality): Lawyers must make reasonable efforts to prevent unauthorized disclosure of client information. A compromised device can leak confidential data, violating this core duty.
Rule 1.1 (Competence): Competence now includes understanding and managing technological risks. Lawyers must stay abreast of threats like Kaleidoscope and take appropriate precautions.
Rule 1.3 (Diligence): Prompt action is required to investigate and remediate breaches, protecting client interests.
Rule 1.4 (Communication): Lawyers must communicate risks and safeguards to clients, including the potential for data breaches and the steps being taken to secure information.
Rules 5.1 & 5.3 (Supervision): Law firm leaders must ensure all personnel, including non-lawyers, adhere to cybersecurity protocols.
Practical Steps for Lawyers – Backed by Ethics and The Tech-Savvy Lawyer.Page

Lawyers: Secure Your Practice Now!
Download Only from Trusted Sources: Only install apps from the Google Play Store, leveraging its built-in protections. Avoid third-party stores, the main source of Kaleidoscope infections.
Review App Permissions: Be vigilant about apps requesting broad permissions, such as “Display over other apps.” These can enable malware to hijack your device.
Secure Devices: Use strong, unique passwords, enable multi-factor authentication, and encrypt devices-simple but essential steps emphasized by our blog posts on VPNs and ABA guidance.
Update Regularly: Keep your operating system and apps up to date to patch vulnerabilities.
Educate and Audit: Train your team about mobile threats and run regular security audits, as highlighted in Cybersecurity Awareness Month posts on The Tech-Savvy Lawyer.Page.
Incident Response: Have a plan for responding to breaches, as required by ABA Formal Opinion 483 and best practices.
Communicate with Clients: Discuss with clients how their information is protected and notify them promptly in the event of a breach, as required by Rule 1.4 and ABA opinions.
Label Confidential Communications: Mark sensitive communications as “privileged” or “confidential,” per ABA guidance.
Advanced Strategies

Lawyers need to have security measures in place to protect client data!
Leverage AI-Powered Security: Use advanced tools for real-time threat detection, as recommended by The Tech-Savvy Lawyer.Page.
VPN and Secure Networks: Avoid public Wi-Fi. But if/when you do be sure to use VPNs (see The Tech-Savvy Lawyer.Page articles on VPNs) to protect data in transit.
Regular Backups: Back up data to mitigate ransomware and other attacks.
By following these steps, lawyers fulfill their ethical duties, protect client data, and safeguard their practice against evolving threats like Kaleidoscope.
Zoom Attack Exposes Lawyers to Major Cyber Risk: Why Vigilance Is Now an Ethical Imperative!

Lawyers need to be able to Spot fake Zoom invites—protect your client data now!
A sophisticated cyberattack targeting Zoom users has recently emerged, with direct implications for lawyers and legal professionals. The attack, detailed by Malwarebytes, involves a crime group dubbed ELUSIVE COMET that lures victims into Zoom meetings and tricks them into granting remote access. This enables the installation of malware and theft of sensitive data, including financial assets and confidential client information, e.g., PII.
How the Attack Works
Attackers pose as reputable contacts (e.g., media invitations) and set up Zoom calls.
During the meeting, the attacker often sends a remote control request with their camera off, disguising their screen name as “Zoom” to appear legitimate.
If the victim approves, the attacker gains full control of the victim’s system, installs malware, and can access files, emails, and even financial accounts.
Why Lawyers Must Be Extra Cautious
Ethical Duties Under ABA Model Rules

You need to be careful who you let into your zoom conferences!
Competence (Rule 1.1): Lawyers must provide competent representation, which now explicitly includes technological competence. Comment 8 to Rule 1.1 states:
To maintain the requisite knowledge and skill, a lawyer should keep abreast of changes in the law and its practice, including the benefits and risks associated with relevant technology, engage in continuing study and education and comply with all continuing legal education requirements to which the lawyer is subject.
Confidentiality (Rule 1.6): Attorneys are ethically obligated to protect client information from unauthorized disclosure. Allowing remote access to your device can expose privileged communications, work product, and sensitive client data to malicious actors.
Failing to maintain technological competence or safeguard client data can result in ethical violations, malpractice claims, and reputational harm.
Best Practices to Prevent Zoom-Based Attacks
Never accept remote control requests from unknown or unverified participants.
Use Zoom via your web browser when possible, as the browser version does not support remote control, reducing risk.
Enable meeting passwords and waiting rooms to control access.
Restrict screen sharing and disable remote control features unless absolutely necessary.
Verify all meeting invitations-scrutinize the sender’s identity, and be wary of unsolicited requests, especially those involving media opportunities or unfamiliar contacts.
Keep Zoom and all security software updated to address known vulnerabilities.
Educate staff and colleagues about the risks and proper protocols for virtual meetings.
What to Do If You Suspect a Breach

You control access—deny hackers, defend your practice.
Disconnect from the internet immediately to limit further access.
Contact your IT or cybersecurity team and initiate your incident response plan.
Notify affected clients and relevant authorities as required by law and ethical rules.
Document the incident and steps taken for compliance and potential reporting obligations.
Review and update your security protocols to prevent future incidents.
Let’s be careful out there - it could cost you your job or, worse yet, your bar license if you don’t!
Happy Lawyering!!!

MICHAEL D.J. EISENBERG IS A WASHINGTON, DC ATTORNEY WHO LOVES HIS TECH.

I've spent years helping lawyers—young and old—tackle their tech challenges. Now, I’m bringing that knowledge to a broader audience with this blog. My posts are inspired by real questions I’ve been asked and the trends shaping the future.
Whether you're a tech novice or a pro, you'll find practical insights here to streamline your legal practice and improve your daily life. Let’s make technology work for you, not against you. 😀
DISCLAIMER: I cannot and do not offer any guarantee of computer hardware, software, services, practice, etc. discussed in this blog. Use at your own risk. Further, I am not offering any legal advice nor do the discussions in this blog create an attorney-client relationship.